What is This Project About?
I built a tool that can crack passwords. The tool takes a scrambled password (called a hash) and tries to find the original password by testing millions of words.
This project helped me understand two important things. First, how attackers break into accounts using weak passwords. Second, why we need to use strong passwords to stay safe.
How Does Password Cracking Work?
When you create a password on a website, the site does not store your actual password. Instead, it scrambles your password into a long random looking text called a hash. For example, the password "pranay" becomes something like "5d41402abc4b2a76b9719d911017c592".
My tool works by taking a list of common passwords (called a wordlist), scrambling each one, and checking if it matches the target hash. If it finds a match, the password is cracked.
The Tools I Used
Rust Programming Language is what I used to write this tool. Rust is fast and safe, which makes it great for security tools.
SHA-256 is the scrambling method (hashing algorithm) I used. It turns any text into a 64 character code.
RockYou Wordlist contains over 14 million real passwords that were leaked from a website. Attackers use lists like this to crack passwords.
Visual Studio Code is where I wrote and tested my code.
How My Tool Works
Here is the simple process my tool follows:

Step 1: Load the target hash (the scrambled password we want to crack)
Step 2: Load the wordlist (millions of common passwords)
Step 3: Split the wordlist into smaller parts so multiple threads can work at the same time
Step 4: Each thread scrambles passwords and checks if they match the target
Step 5: If a match is found, display the cracked password
Making It Fast with Multithreading
Testing 14 million passwords one by one would take a long time. To speed things up, I used multithreading. This means the program runs multiple workers at the same time, each testing different passwords.
Think of it like having 8 people searching through a phone book instead of just 1 person. The work gets done 8 times faster.
In Rust, I used two special tools for this:
Arc lets multiple workers share the same data safely. All workers need to see the target hash, so Arc helps them share it without problems.
Mutex makes sure only one worker can update the result at a time. When a worker finds the password, Mutex prevents other workers from overwriting the answer.
Testing the Tool
Test 1: Cracking "pranay"
I tested my own name since it happens to be in the wordlist.
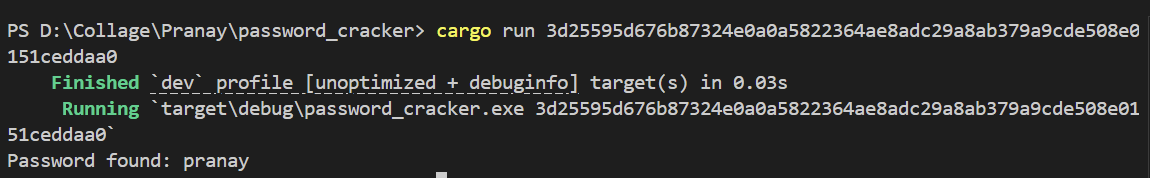 The tool found the password "pranay" instantly
The tool found the password "pranay" instantly
Result: Password cracked instantly!
Test 2: Cracking "password1234"
This is a very common weak password that many people use.
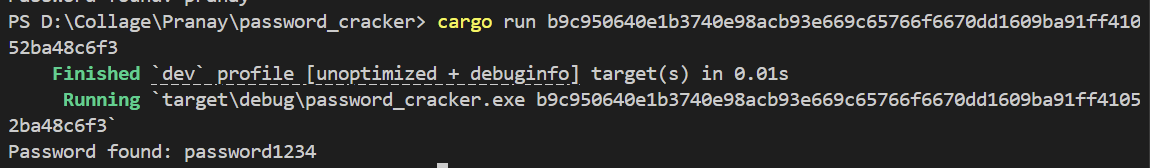 The tool cracked "password1234" in seconds
The tool cracked "password1234" in seconds
Result: Password cracked in seconds!
Test 3: Testing a Strong Password "Rise@2k21"
I also tested a strong password that is not in any wordlist.
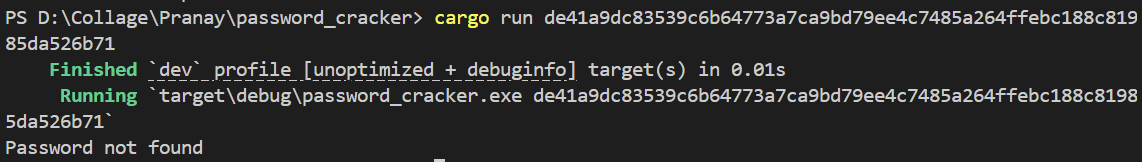 The tool could not find "Rise@2k21" because it is not in the wordlist
The tool could not find "Rise@2k21" because it is not in the wordlist
Result: Password NOT found. This proves unique passwords are safe from dictionary attacks!
Types of Password Attacks
My tool uses a dictionary attack, which tries words from a list. But there are other methods attackers use:
Dictionary Attack tries common words and passwords. It is fast but only works if your password is in the list.
Brute Force tries every possible combination like aaaa, aaab, aaac. It is very slow but will eventually find any password.
Rainbow Tables use pre-calculated answers to find passwords instantly. Adding salt to passwords defeats this attack.
Credential Stuffing uses leaked passwords from other websites. This is why you should never reuse passwords.
How to Protect Your Passwords
After building this tool, I learned what makes a password safe:
Use long passwords. A 16 character password is much harder to crack than an 8 character one.
Use unique passwords. Do not use words that appear in dictionaries or common password lists.
Never reuse passwords. If one site gets hacked, attackers will try your password on other sites.
Use a password manager. It creates and remembers strong random passwords for you.
What I Learned
Building this tool taught me several valuable skills:
Rust programming including how to work with files, threads, and external libraries.
Cryptography basics like how hashing works and why it is used for passwords.
Parallel processing to make programs run faster by using multiple CPU cores.
Security awareness by understanding how attackers think so I can defend better.
Ethical Note
Password cracking tools can be used for good or bad purposes.
Good uses: Testing password strength, security audits with permission, learning about cybersecurity.
Bad uses: Hacking into accounts without permission, stealing credentials.
Always get permission before testing any system. Unauthorized access is illegal.
Conclusion
This project showed me why password security matters. A simple tool running on a laptop can crack common passwords in seconds. The only defense is using strong, unique passwords that do not appear in any wordlist.
If your password can be found in a dictionary or is something simple like "password123", it can be cracked almost instantly. Stay safe by using long random passwords and a password manager.